Organizations of all types and sizes are battling against cyber attackers. In recent years, we’ve seen cyberattacks growing more sophisticated, which makes it harder to detect and mitigate them.
Current methods that organizations primarily use to verify the protection of their systems are vulnerability scans and penetration tests. The results are used for risk assessment that have become mandatory provisions in various regulations (e.g., GDPR and NYCRR). Vulnerability scans and penetration tests are useful for obtaining insight into the security posture of an organization—at a specific point in time.
However, they do not present the full picture; especially when it comes to sophisticated, multi-vector attacks.
Cymulate, rated the "Best cutting edge breach and attack simulation platform" by Cyber Defense Magazine, lets you protect your organization at the click of a button. It was developed to automate the PENtesting process and provide instant results.
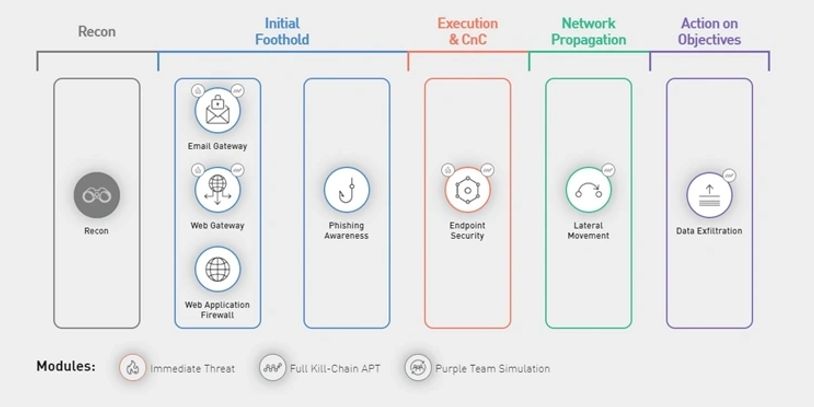
Operating thousands of attack strategies against the Full Unified Kill Chain, Cymulate shows you exactly where you’re exposed, and how to fix it.