Continuous SECURITY POSTURE MANAGEMENT WITH CYMULATE
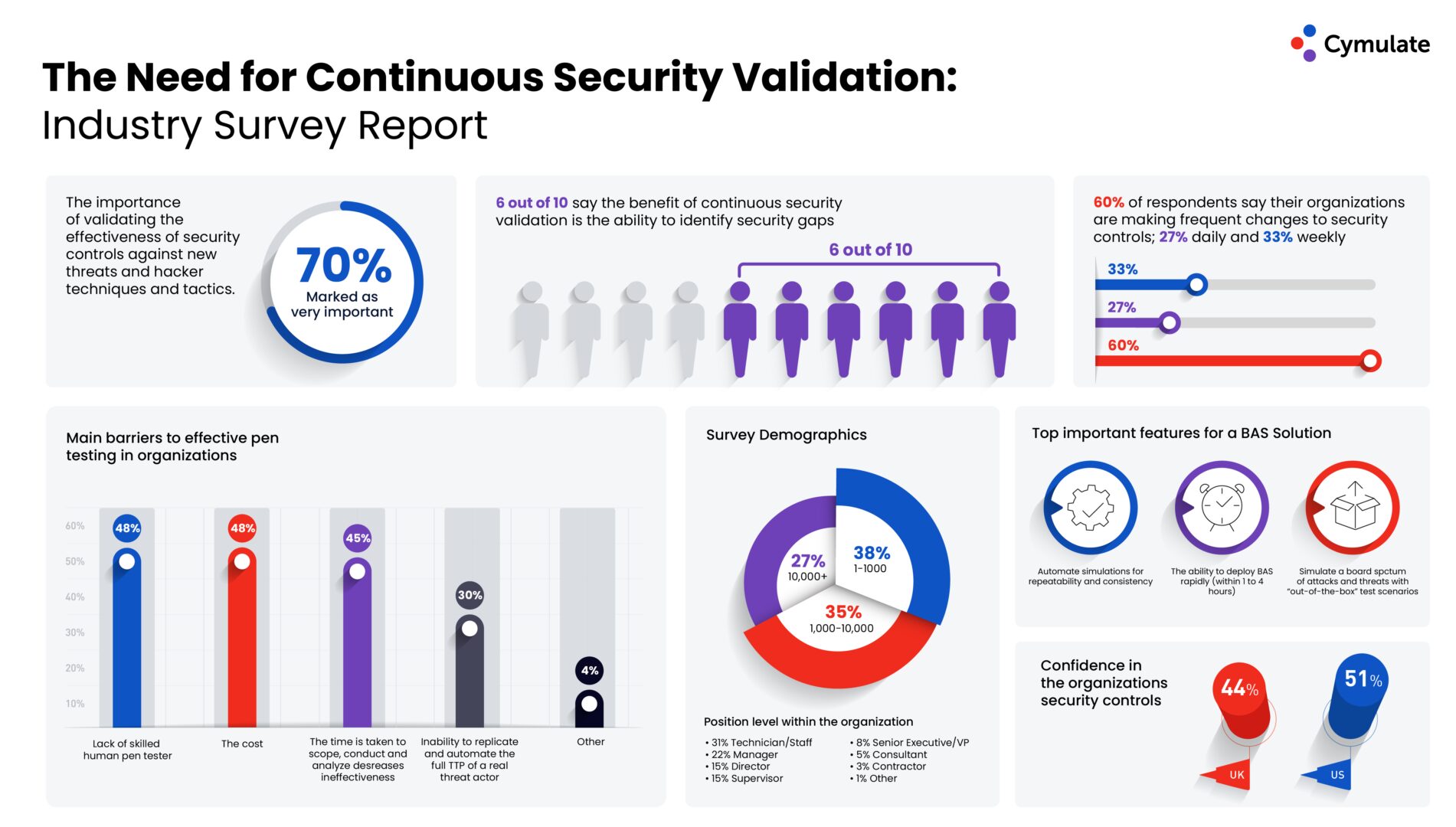
What's Your Company's Real Security Posture?
How confident are you that your organization is protected from the next cyber-attack?
There are multiple factors to consider when answering this question—Exposed digital assets, poorly configured security controls, immediate threats, newly discovered vulnerabilities, security gaps, architecture changes, and more. Your organization’s security posture is affected by many different variables—both known and unknown—that are constantly changing and causing perpetual drift. Maintaining a robust security posture and keeping risk low requires you to continuously monitor your security program’s performance, end-to-end.
Current methods that organizations primarily use to verify the protection of their systems are vulnerability scans and penetration tests. The results are used for risk assessment that have become mandatory provisions in various regulations (e.g., GDPR and NYCRR). Vulnerability scans and penetration tests are useful for obtaining insight into the security posture of an organization—at a specific point in time.
However, they do not present the full picture; especially when it comes to sophisticated, multi-vector attacks.
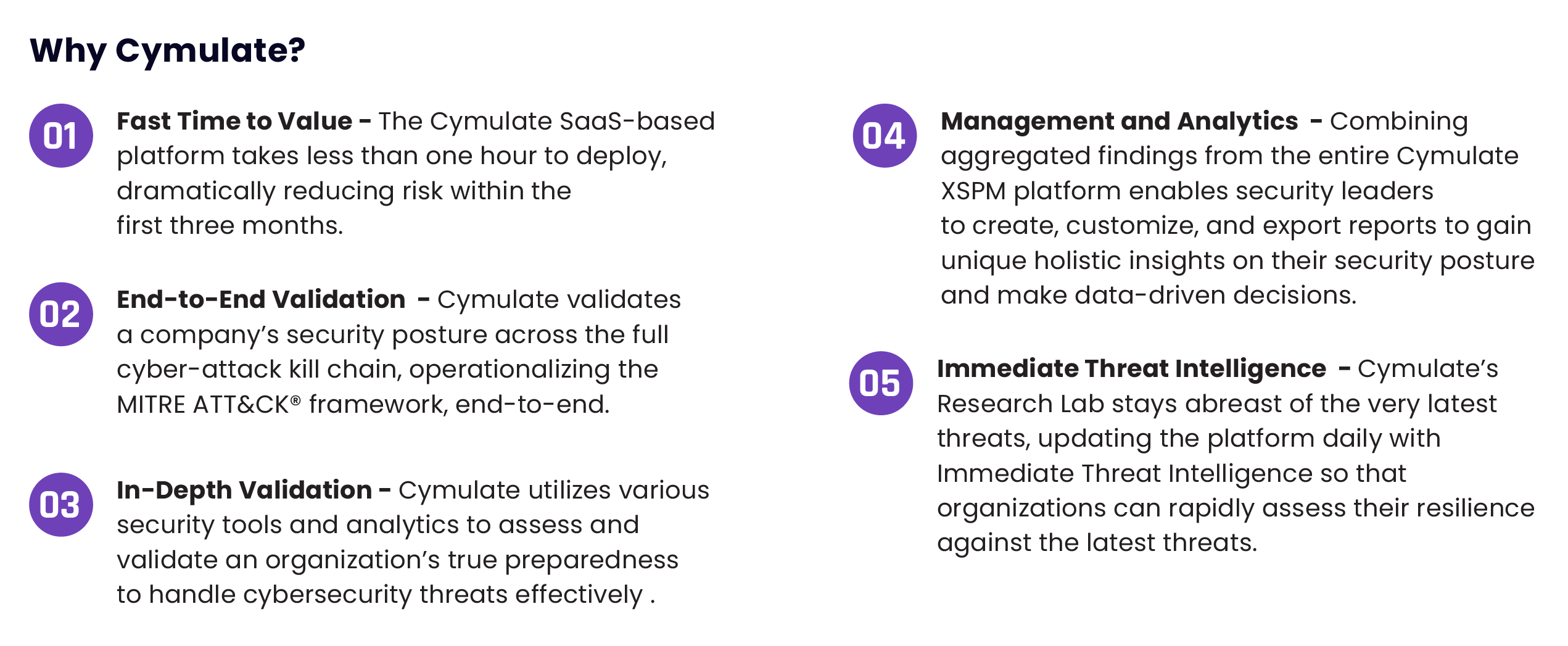
Rated the “Best cutting-edge breach and attack simulation platform” by Cyber Defense Magazine, Cymulate’s platform empowers security leaders to maximize operational efficiency while minimizing risk exposure with a continuous security assurance program. Cymulate’s SaaS–based Continuous Security Posture Management technology helps security leaders manage exposure to cyber threats, map and block possible breach routes, and validate security controls’ effectiveness.
Deployed within an hour, security professionals can continuously challenge, validate and optimize their cyber–security posture across the MITRE ATT&CK® framework.
Cymulate provides simple, out–of–the–box risk assessments for all maturity levels and generates a framework to create customized red and purple teaming exercises by generating tailor–made advanced attack scenarios and campaigns.
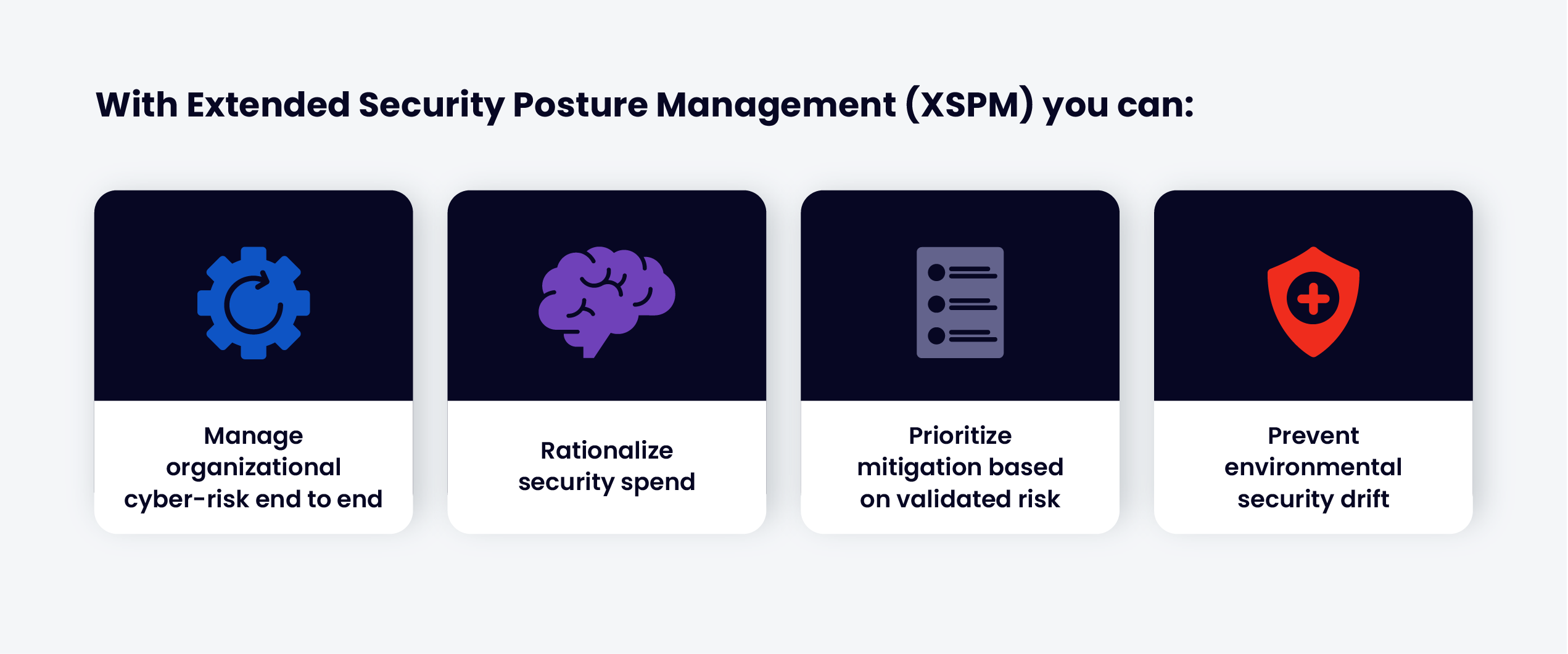

Key Benefits:
-
Gain visibility into your security posture 24x7
-
Improve your security stance
-
Validate the effectiveness of your security controls
-
Meet compliance mandates
-
Rationalize security investments
-
Test against the latest threats as they emerge
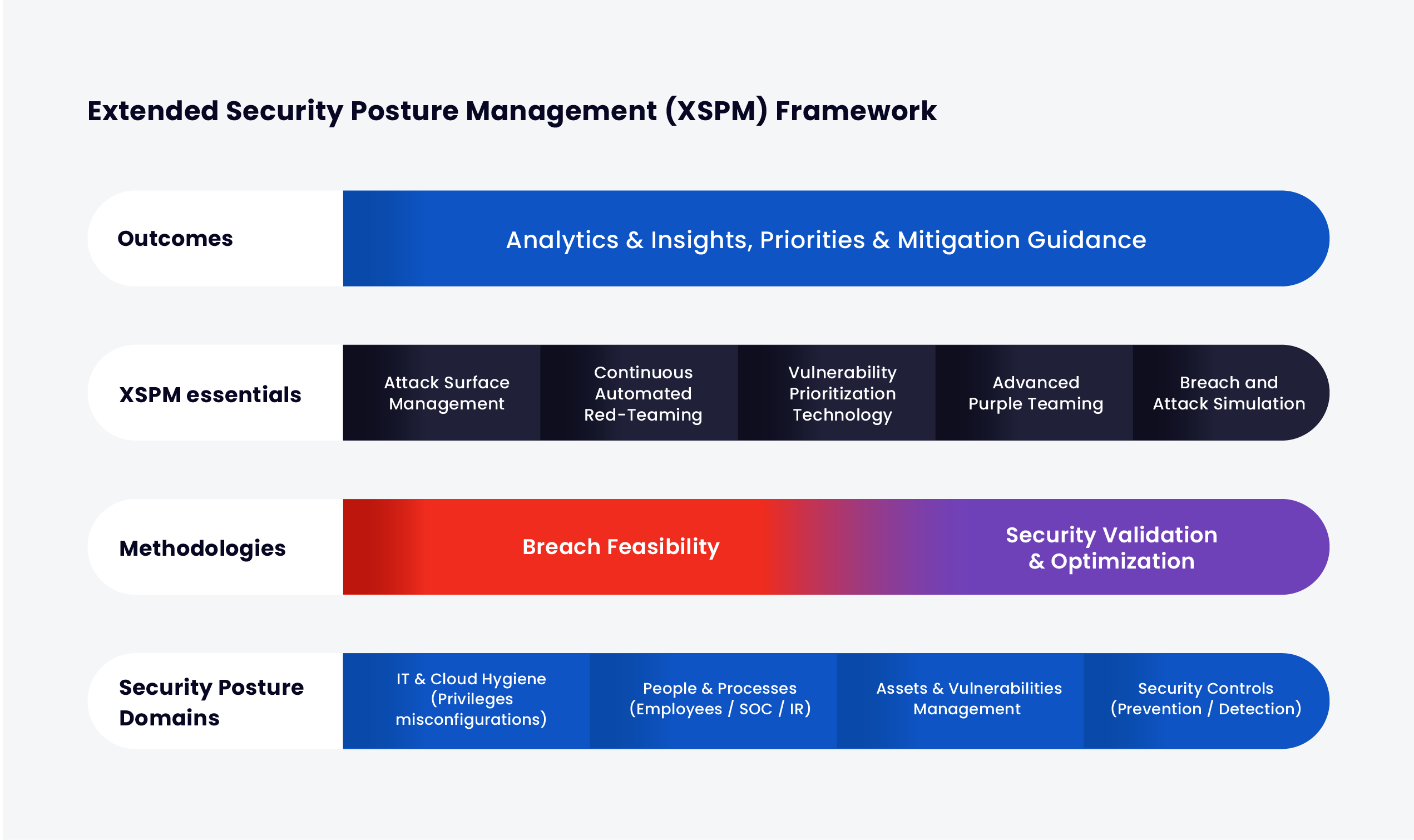
The Most Comprehensive Security Validation Technology
Cymulate’s platform provides an end-to-end overview of an organization’s security posture. This framework presents a comprehensive understanding of current levels of risk, exposure, drift, and even potential savings.


Customer Testimonial